New virus spreads around the world in hours.
On May 12, 2017, a computer virus was detected in Asia. Within hours of its identification, the virus had spread around the world attacking Microsoft operating systems and encrypting computer after computer.
WannaCry was a new virus. Anti-virus and cyber security companies generally fight malware and viruses by identifying pieces of code from older viruses and shutting down the attack. A new virus, often called a “zero-day” exploit is something completely unfamiliar to cyber security programs and hence not detectable.
WannaCry programming was not completely new, however. It was created using an exploit called EternalBlue. The EternalBlue exploit used a flaw in Microsoft’s programming to hack computers. Who created this EternalBlue program? The United States Government. The NSA had discovered the flaw and created the exploit years before.
The NSA did not tell Microsoft about the flaw until February of 2017. Why tell them after all these years? Because it had recently been stolen from the NSA and was out in the public somewhere. Microsoft released a security patch that corrected the programming flaw in March of 2017. By April of 2017 a hacker group had posted the EternalBlue exploit, and it was widely available.
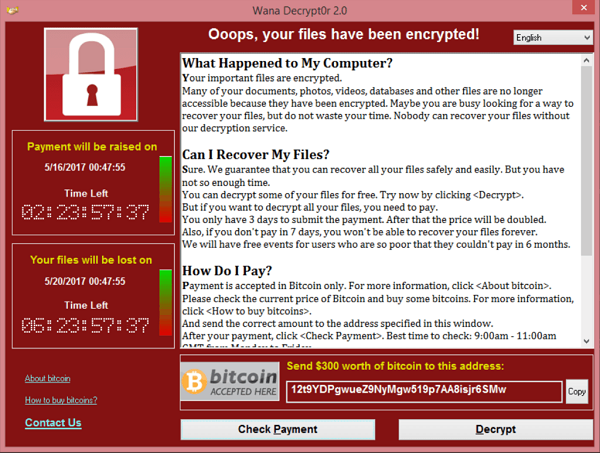
The WannaCry virus began spreading on the morning of May 12, 2017. It was a worm virus, which spread from one computer to another on its own. Once a new computer was infected, all the files on the machine would be encrypted and a message would appear to pay Bitcoin to the perps if you wanted to get your files released.
Within hours over 200,000 computers around the world were infected with WannaCry. The infected computers all had one thing in common. They had not downloaded the March Microsoft security patch that addressed the EternalBlue exploit (always make sure your computer’s updates are current). Cyber security experts around the world worked furiously to find a way to shut down WannaCry.
About 8 hours after WannaCry was detected, Marcus Hutchins, a 23-year-old British cyber security buff and researcher figured out how to stop the virus from his computer in his bedroom. He discovered a killswitch that had been left in the code of the virus and was essentially able to turn it off. The WannaCry virus needed to communicate with a website to function. The domain name for the website was not registered. Hutchins registered the site and took it over. He was able to intercept and mimic communication from infected computers and stop the spread.
The crisis was averted for the time being. Several other versions of WannaCry were created, but security experts had the upper hand. The NSA identified North Korea as the likely originator of the virus. Marcus Hutchins himself was arrested by the NSA several months after stopping the WannaCry initial exploit. He had created a bank credential stealing program in 2014 and had been profiting from it for years.
by Christopher Flanagan